United Security Products 10-4 manuels
Manuels d'utilisation et guides de l'utilisateur pour Téléphones United Security Products 10-4.
Nous fournissons des manuels en pdf 2 United Security Products 10-4 à télécharger gratuitement par type de document : Spécifications, Manuel du propriétaire

United security products 10-4 Spécifications (430 pages)
marque: United-security-products | Catégorie: Téléphones | Taille: 1.85 MB |

Table des matières
◆ The body
21
Chapter 3
42
Chapter 5
62
Configuring URLs
101
Chapter 6
102
To remove a URL
105
◆ Grace interval
145
Chapter 8
160
◆ Yellow
181
◆ Orange
181
/url_name.ext
190
◆ Ignore value
196
◆ XML value
197
Chapter 11
222
Chapter 12
268
Chapter 13
296
Chapter 15
320
Viewing charts
322
RFC violations
337
Appendix A
338
Input violations
342
Signatures
365
Appendix C
382
Configuration
383
Appendix D
386
Important
393
Appendix F
400
Glossary
401
Glossary - 1
403
Glossary - 2
404
Glossary - 3
405
Glossary - 4
406
Glossary - 5
407
Glossary - 6
408
Glossary - 7
409
Glossary - 8
410
Glossary - 9
411
Glossary - 10
412
Glossary - 11
413

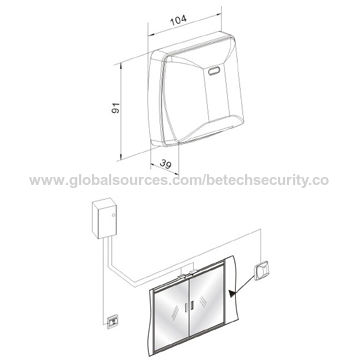
United security products 10-4 Manuel du propriétaire (24 pages)
marque: United-security-products | Catégorie: Téléphones | Taille: 0.53 MB |

Table des matières
United Security Products appareils